GDPR and encryption
Note that this article is for informational purposes only. It is not intended to and should not be relied upon or construed as legal advice. You should not act or refrain from acting on the basis of any content in this article without seeking legal or other professional advice.
Read also:
Encryption is a powerful tool to protect personal data and this is the main reason why the GDPR explicitly refers to encryption in several articles.
The fact that encryption is mentioned many times in the new regulation brought many people to think it’s a mandatory requirement for the compliance. But we’ll see that it’s not the case.
The GDPR protect European residents and their personal data and this purpose is much wider than the adoption of a set of security technologies. Adopting encryption is certainly useful to comply with the GDPR but it’s not mandatory nor it represents a sufficient measure to be compliant.
Let’s see two example to better understand the point:
- ACME Inc. adopted database encryption for the customers DB of its accounting software. Despite this, the admin password of the solution is shared and accessible by all the employees and it’s not periodically changed.
- Instead, BIG Llc. invested in training in order to protect personal data and enforced a severe set of policies for password management and access to both physical machines and digital touchpoints to the customers database, despite not having adopted any encryption technology.
What do you think, can we consider ACME Inc. a GDPR-compliant business? What company would you trust more? While it would be safer to have an encrypted database, we would prefer the second one.
Ultimately, what really matters is the protection of personal data of EU residents and the GDPR doesn’t specify how to ensure it: the regulation requires the adoption of adequate measures, compared to the risks, and businesses will have to demonstrate the compliance with the principles of protection.
So, is encryption required at all?
Not necessarily, but it’s very probable that encryption could be a required measure to protect the personal data managed by your company from external threats.
Simply, encryption doesn’t have to be adopted at all the possible levels, for all the available data and, for sure, it’s not the solely measure to adopt.
First of all, it’s important to introduce robust processes and policies for data protection. Regarding this, we suggest to read our previous article about the GDPR compliance.
You should also consider that encryption protect data but limits their availability, slow down write and read operations and can – in case the encryption keys would be lost – cause a data loss. For this reason we suggest to follow the best practices in order to get the most from your storage infrastructure and protect the data.
Encrypt physical drives
Encrypting physical drives allows to protect personal data from thefts, losses or not-procedurally-correct dismissions of physical machines.
All the main platforms, mobile included, and most of NAS, SAN and other storage devices, support real time encryption at disc-level.
Drive encryption is a time efficient and powerful solution. We suggest to adopt it on all the machines with business-critical and/or personal data.
For Windows physical machines we suggest to enable BitLocker. You can find more info about the technology here.
Talking about NAS, each manufacturer has a proprietary management system so the procedure to enable encryption differs widely. The following video comes from the popular company QNAP, which offers a user-friendly solution to encrypt volumes:
Encrypt databases
All the main database solutions have the ability to encrypt “data at rest”, which are db files stored on a physical or virtual disk. This allows to protect their content and so the data subjects in case the db files will fall into the wrong hands.
You can find a guide to encryption functionalities of Microsoft SQL Server here.
As already explained above, encrypting database files is not enough to ensure data protection. Regularly updates of the engine, restricting db management to a list of IPs, enacting strict policies for administrator access, adopting strong passwords and change them often are all good practices to avoid unpleasant accidents and can be considered measures for the GDPR compliance.
Encrypt data with Uranium Backup
Uranium Backup allows to encrypt all the data saved in a common destination to back up data in remote repositories like a cloud destination, we suggest to perform chain backups in remote repositories like a cloud destination.
Data must be zip compressed, following the procedure explained in the screenshots below:
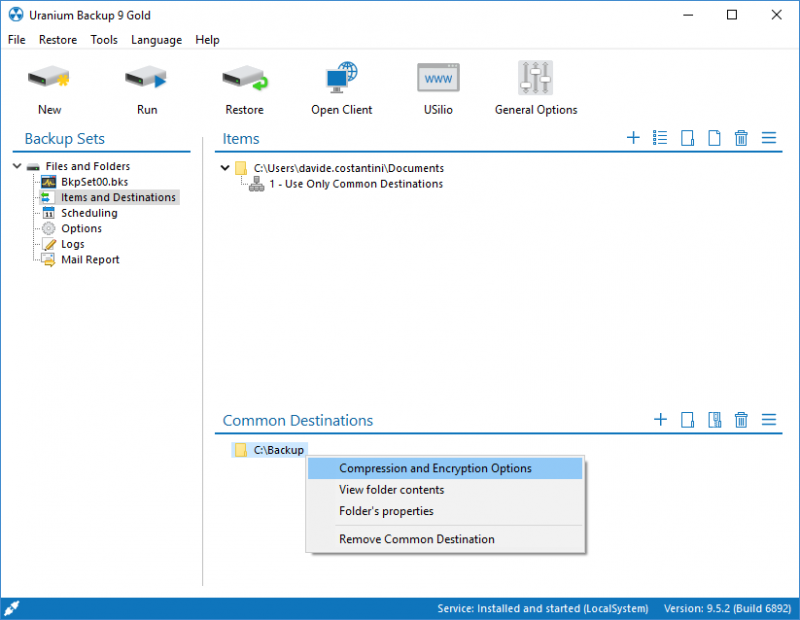
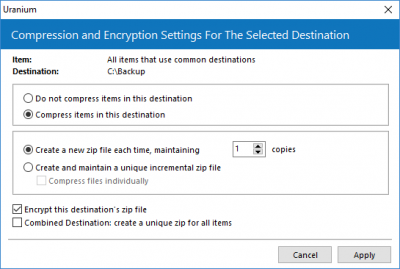
The encryption password must be specified before executing the backup, you can find it in the General Option of Uranium Backup. In case you forgot to configure it, Uranium will use an auto-generated password and it will still be able to recover data from the same client who performed the encryption, using the restore utility (but you won’t be able to recover data from another Uranium client and you will be exposed to data losses in case of failure of the backup machine):
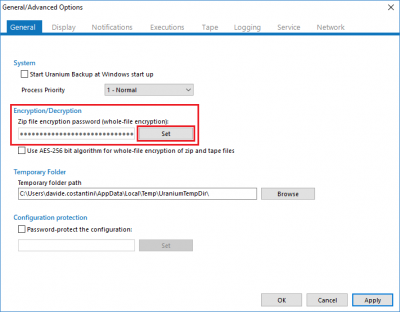

 Français
Français
 Italiano
Italiano
 Español
Español